CVE-2010-3333 Microsoft RTF stack overflow vulnerability
The case from 《漏洞战争》, this article is for notes only.
Testing Environment
System:Windows XP SP3
Vulnerable software:Microsoft Office Word 2003 SP3 [download]
Debugger:Windbg
Testing Poc
Use Metasploit to generate test poc:
1 | search cve-2010-3333 |
set target 6 is used to generate crash poc.
Analysis
Open Word, attach the process with windbg and then open msf.rtf.
You will find crash occurred at 30e9eb88.
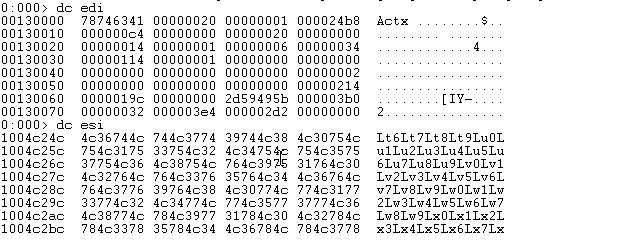
rep movs is used copy [esi] to [edi].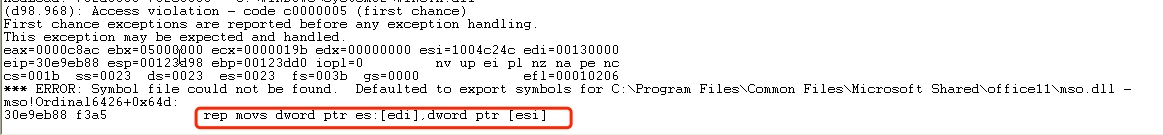
The cause of crash because data in the [esi] is too long. After multiple copies, edi eventually points to a non-writable memory area, triggering an exception.
Use stack backtracking,locate the crash function which function calls: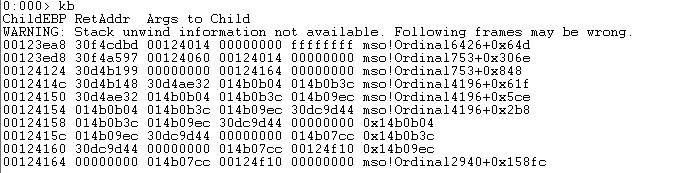
Found previous function call: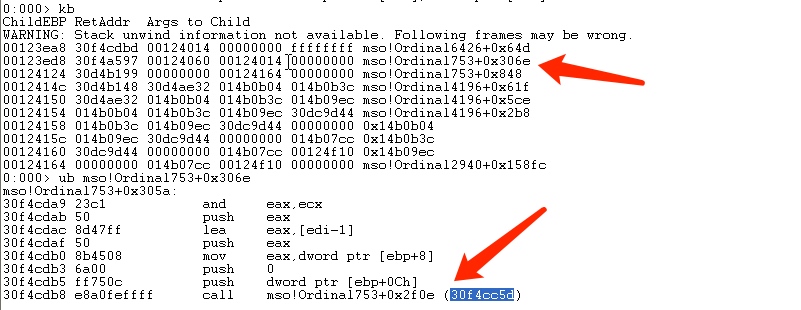
Continue to track the function 30f4cc5d:
We have found function 30e9eb62 at inside 30f4cc5d.( rep movs located in 30e9eb62)
So,that is the vulnerable function.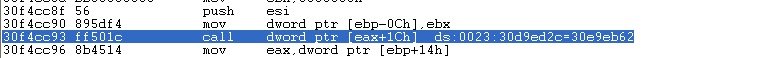
Exploitation
Run to the vulnerability instruction: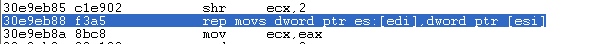
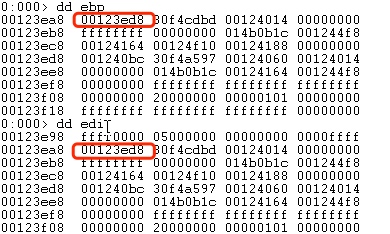
You can be seen that edi is very close to ebp, only 16 bytes apart. Without considering like as DEP and GS… you can override the return address as jmp esp.